
Last Lecture: Security II
By:Brian Yeh, Ryan Gochee ,David Hwang, Lee Chou
Keys
There are two popular ways to encrypt data:
Table of Asymmetric Encryption

What the table above says is if you have data (P) and a public key (U), you can easily encrypt it to ({P}U). If you have the encrypted data {P}U and the private key (K), you can easily decrypt the data (P). However, if you have the encrypted data {P}U but only have a public key (U), you cannot easily decrypt it (P). Also if you only have the public key (U), you cannot figure out the private key easily (K).
What are the disadvantages of using public keys (asymmetric encryption)?
-It is slower.
-It doesn’t solve the key distribution problem; it only changes it.
Example: Symmetric Encryption
Alice and Bob want to talk; they share a secret key, K. (symmetric encryption)
Alice communicates to Bob with "Im Alice" and encrypts the message using private key, K. Then Bob communicates to Alice, "OK".
![]()
However, what if Eve was eavesdropping? Then, she can intercept the message and act if she was Alice to Bob.
![]()
To prevent the situation in Example 1 form happening, we use a nonce (a random beautiful bit string).
Example: Symmetric Encryption using Nonces
After Alice sends Bob, “I’m "Alice", Bob will send Alice a nonce. Then Alice must send the nonce back to Bob, in encrypted form. Then, Bob will receive the encrypted nonce back and decrypt it. If the nonce he sent is the same as the one he receives back, then he will know for sure that Alice is truly Alice.
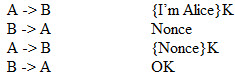
Even if Eve intercepts Nonce and {Nonce}K, Eve should not be able to calculate K.
Integrity + Authentication + Privacy
A message authentication code (MAC) is used to authenticate a message.
One such algorithm used to produce such messages is the HMAC algorithm. Use of the HMAC algorithm assumes a shared secret key K. M is the message. pad1 and pad2 are random pads of characters. The output of the HMAC algorithm will output 160 bytes.
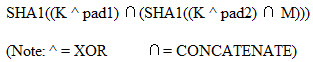
The sender attaches this code to the message. Then the receiver calculates the code itself and compares it to the code it received. If what it calculated and what it received are not the same, it means the message’s integrity was compromised.
We do not get privacy with just using a MAC alone. The eavesdropper can still see the message. Therefore, when we send a message M, we encrypt it with the shared secret key K.
![]()
However, there are costs to attaining integrity and privacy. The overhead is 24% which is a large energy drain.
Below is an example of a typical authentication session using asymmetric encryption.
Example: Asymmetric Encryption using Nonces
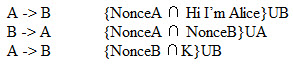
Note: Only A knows A’s private key, UA. Likewise, B only knows B’s private key, UB. Also, K is a shared key used for only this session.
SSH Protocol/Implementation
From a users viewpoint:
client: ~/.ssh/id_rsa.pub
id_rsa
known_hosts
id_rsa.pub is the public key
id_rsa is the private key (do not copy it or open it, leave on disk
known_hosts has the servers you want to talk to and its public keys
From a servers viewpoint:
server: ~/.ssh/authorized_keys
The server holds authorized host names and public keys.
Example:
Imagine a client as the client. The Treasury Central Bank account is the server.
What if the clients laptop is stolen? Then someone else has the clients private key and that would seem to be bad.
However, the clients private key is encrypted with a passphrase that only the client would know (in their head).
IPsec
Basic concept:
Go one level lower: make the network secure, and leave the applications alone.
The major idea is to have internal network nodes all trust each other, and build an internal virtual network using a shared secret key.
From the application’s point of view:
Unencrypted packets are sent atop a virtual network.
As this protocol is intended for use by large organizations and networks, and also does cost money unlike the free ssh, IPsec is not widely used by college students.
Authorization and Access Control
Access control is how an operating system keeps track of who can do what.
Related factors are:
Privacy: reading files
Integrity: writing files
Trust: access permissions
Access Control Lists (ACLs)
-these keep track of which users have which permissions on which files and objects.
The simplest way is to use a 3D bit array, in which each user would map to an object and also map to a set of permissions associated with that object.
Problems with a 3D bit array:
-too unwieldy and the large size of it is impractical
The UNIX model is to use the 9(+) bits for read, write, and execute access for user, group, and world: the drwxr-x-r-x string often found when using ls –l.
Problems with the UNIX model:
-oversimplified and cannot handle very specific permissions for certain users
Another model uses a linked list of sorts of keep track of users and their permissions for a certain object, as below:
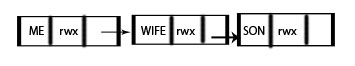
One can inspect ACLs on Solaris by using the commands getfacl and setfacl.
However, this type of ACL can also be very long, and hard to manage.
Another alternative:
Role Based Access Control (RBAC)
These are ACLs that contain roles, instead of users. A role could be something like “administrator”, “grader”, “moderator”, or “technician”. Then, for each user, there is a list of roles that it can assume, and each role has certain privileges. Each session would have a role that the user would assume. Now, the ACLs would be shorter due to only having to keep track of which users could access certain roles, and each role would have actions that they could execute on the system. For example, an dangerous unlink call such as unlink(“d1/d2”); would only be available to system restorers.
Example: file descriptor
Two examples to implement a capability:
example: Ken Thompson's trick
login.c:
If (strcmp(u, "Ken") == 0)
return 0;
gcc.c:
if (compiling "login")
insert above login.c code;
if (compiling "gcc")
insert this code;
Define what you trust and make sure it's safe, but realize that no matter what, you have to trust something.
Note that these also apply to other computer systems, e.g. network (Apache), and database (Oracle) systems
Something to think about: is Linux Object-Oriented? It was written in C, but what if it was written in C++?