CS 111 Operating System Principles
Lecture on 12/1/2009
SECURITY
Assembled by Jiayan Jiang, Weiguang Si
Know Your Enemy: Threat Modeling + Classification
(To Come Up with Defense Mechanisms)
A Case Study: Courseweb Threats
Students (ordinary users) want to see each other’s work to plagiarize. Outsiders want to gain personal information about students or copies of assignments.
Mode of attack:
1). guess passwords of legitimate users
2). exploit an Apache bug (or other infrastructure bug), e.g. SQL injection
3). Denial of Service (DoS)
4). social engineering (trick someone into a password)
5). take over a router
6). break into the machine room and steal a disk (backup tape)
7). video cam snapping PINs
8). key logger on terminals
9). insider attack
General OS Functions
Authentication: prove who you are
Integrity: don’t let attackers muck with data or metadata (especially security metadata).
Authorization: are you allowed to do that?
Auditing: keep logs, so that you can figure out what bad guys (especially insiders) did and undo bad guy’s actions.
Constraints:
Efficiency: especially to avoid DoS problems
Correctness: because code/users are adversaries.
Authentications
(Prevents Masquerading)
Based on:
who the principal (user in charge of the session) is (e.g. retinal scan)
what the principal knows (e.g. passwords)
what the principal has (e.g. physical keys)
These three ways are often combined, and you can use one to bootstrap another.
Techniques:
external: e.g. by login program (passwords & tokens)
internal: OS must keep track of user’s identity. Integrity must be respected. Consulted for authorization decision, logged during audits.
Building Blocks:
cryptographic hash functions
+ symmetric encryption
+ asymmetric encryption (more expensive)
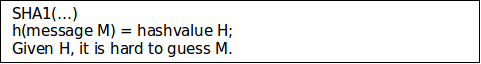
cryptographic hash functions example:

symmetric encryption example:
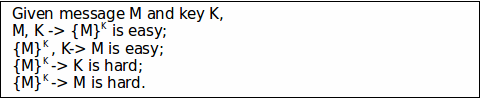
asymmetric encryption example:

A Typical Conversation: A wants to talk to B
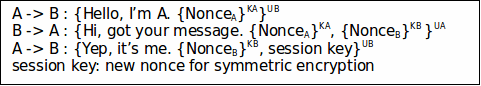
SSH (http://en.wikipedia.org/wiki/Secure_Shell) does this.
Authorization
Access control:

This is too hard to administrate.
We want to shorten the authorization metadata by making it easier to maintain and understand, but the underlying model might be more complicated.