NFS servers distribute their file system across a number of disks. This distribution gives them lots of extra space, and the ability to parallelize reads, but it comes at a cost. As the file system gets larger, the problem of correctly handling all of the disks becomes more and more complex. The system is also vulnerable to media faults. Only one block of the server's disks has to fail for the system to become unreliable. File systems can be finely tuned in order to handle power outages and such, but if we want a truly reliable system, we have to find a way of dealing with media faults.
10TB drive = $2000
1TB drive = $100 ~ 10 1TB drives = $1000
It is often cheaper to build a large drive out of lots of smaller ones. If the bid drive fails the system is trashed, but if the smaller drives are set up with some redundancy, a media fault is no problem. Simply replace the failed drive and restore the data via the redundancy.
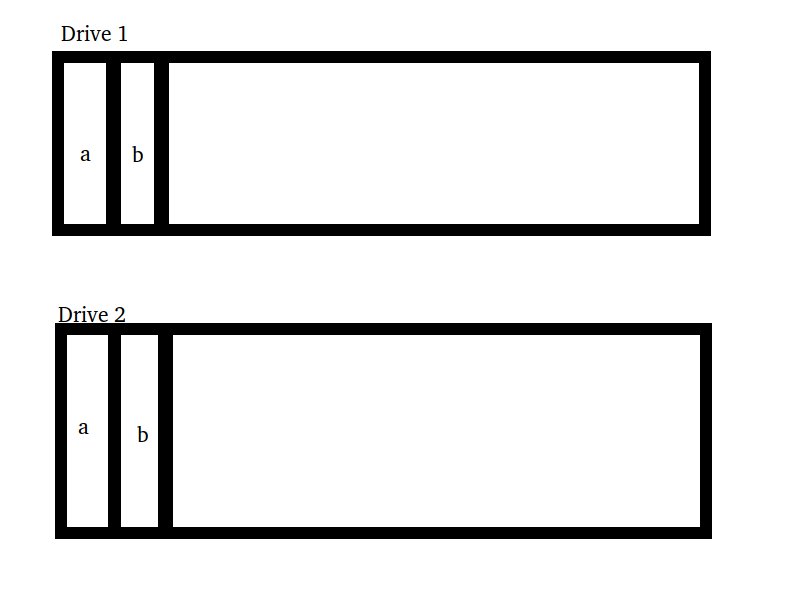
There are two way to combine a number of smaller drives into a larger one. Either concatenate the smaller drives, or stripe file system's data onto the disks. If reads remain relatively local, this striping allows us to parallelize reads. Despite this, Raid 0 still doesn't handle the origianal reliability problem


concatenation on the left, striping on the right
If we have two copies of the data, it's not a problem if one drive crashes. Raid 1 is simply two hard drives that mirror each other. This handles the reliability problem and additionally allows for two times the read throughput
Mirroring, concatenation, and striping can all be combined arbitrarily. These ideas are combined to form the basis of Raid 4 and Raid 5. Concatenation at the top level allows for easiest expansion of drive size.
Given N drives, Raid 4 stores data on N-1 of the drives. The Nth drive is called the parity drive. An example best illustrates how its' data is determined.
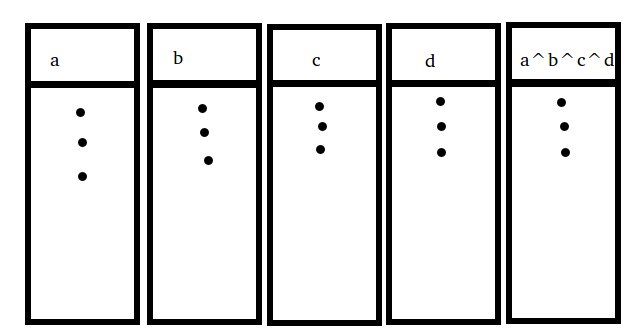
If the drive with bit B fails, its' bits can be calculated by A^C^D^Parity. Also noticethat Raid 1 is simply N=2. Raid 4 is cheaper that Raid 1, since less drive space is used to backup the others. Writes are more expensive and this extra cost scales with N, but this performance hit can be minimized with caching. Writing to the parity drive, however, is a bottleneck, as each bit has to be calculated.
Raid 5 is nearly identical to Raid 4, but it stripes the parity bit accross all the drives. This makes it difficult to add drives to Raid 5.
The Supreme Council is an arm of the Iranian government that controls "all" data flow into Iran, and reports to the Supreme Leader. Recently, they launched a DoS attack on the BBC, ultimately jamming some satellites
There are three kinds of attacks. Attacks against privacy attempt to release privilaged information. Attacks against file integrity attempt to tamper with the victim's data. Attacks against service attempt to deny service. File integrity is the most important of these to guard against, followed closely by privacy and then service.
In defense, our general goals should be to deny unauthorized access, allow authorized access, and be able to handle lot of 'bogus' requests. Denying unauthorized access is obvious but difficult to test for, while allowing authorized access isn't obvious but is natural to test for. 'Bogus' requests can be simulated, so preparing for a DoS can be done.
Minimize what needs to be secret. Don't assume that the bad guys won't learn your design either. These seem obvious, but take DVDs for example. They used a single encoding scheme, so the plan got out, there was nothing else they could do.
External authentication occurs when an outsider wants inside. Examples include passwords, physical keys, and finger prints. Note that all of these can be cracked. Sometimes two forms of authentication are required in order to increase security.
Internal authentication or simply authorization occurs when an insider tries to access components, like a user id in a process table entry