Security and Confidentiality
Data has become an integral part of our society today. Whether it is bank account information, or legal documents, we expect our data to be safe and secure. Security has progressed over the years, but the thing we find most common are passwords. Passwords are the hidden authentication of ourselves in various applications today. Passwords are one initial layer of security, but ultimately aren't without flaws. Making them more complex tends to tighten this security flaw. XKCD highlights what really is important in complexity in passwords.
Methods of Intrusion
Here are some of the basic methods in which vulnerabilities are exploited:- Brute Force - This method, the most basic, involves guessing passwords or keys by repeatedly trying many such character combinations.
- Unauthorized Monitoring - This method involves monitoring say network packets, or key strokes through malicious software, ultimately to gain access to your data.
- Imposters - Having data be sent to something that the user isn't actually intending it to go to.
Authentication
There are two main types of authentication seen today, internal and external. External authentication is the creation of credentials in a system, i.e. a username and password, which are used to authenticate your access to files. Internal authentication is a way to keep track of the actions your perform, for something that could later be audited. Keeping track of these types of authentication allows the server to know who has access to what, and what was actually accessed incase malicious behavior occurs and needs to be corrected in the future. This example from the book shows an example of this authentication process.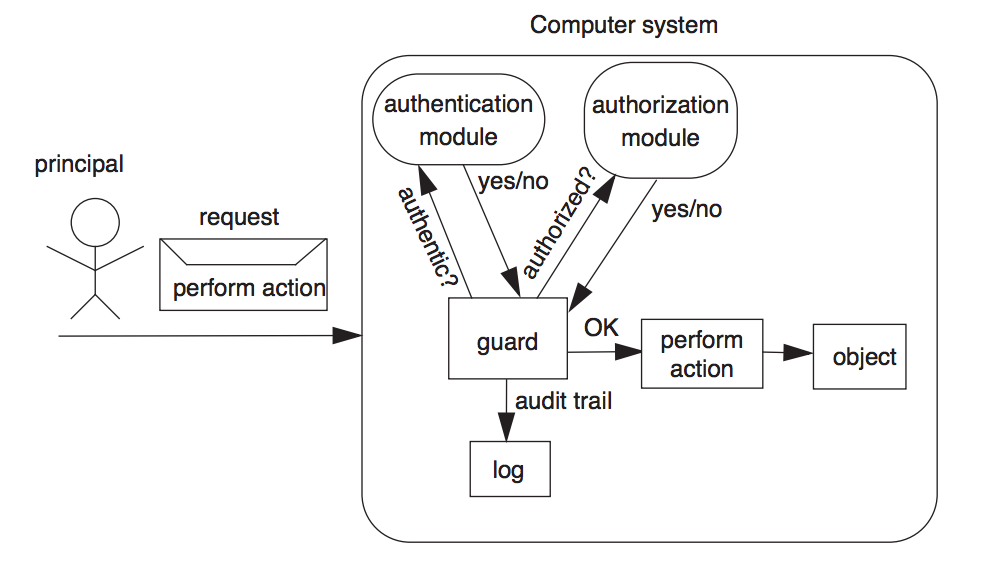
These credentials are associated with permissions. The most basic example is seen with file permissions in linux. They can be set with chown, and the user can have different privileges in read, write, and execution. Other higher level examples seen are things such as access control in Apache, where authentication is determined by where you are requesting the file from.
Encryption and Protocols
This is a way to further allow for authentication, without some of the password insecurities. When sending a password over a network, it could be easily looked at. In HTTP for example, this would involve sending a password in plain text. HTTPS on the other hand encrypts this password, so someone looking at the network packets can't see your password directly. In HTTPS for example we use a Cryptographically Secure Hash Function. A hash function is used to take plain text, and convert it to an noninvertible hash value, which is usually a string of characters. Another usage of hash functions involves public/private key authentication, a public key is shared to the server, which is used to decrypt the private key resulting in a successful "handshake" of authentication. Sending hashes ultimately cuts down on the flaws that comes from plain text passwords. One such hash algorithm is the SHA algorithm. The distribution of these hashes, or keys is a general example of a security protocol. This example from the book shows the process of security when signing, i.e. encrypting, and verifying, i.e. decrypting occurs in message transfer.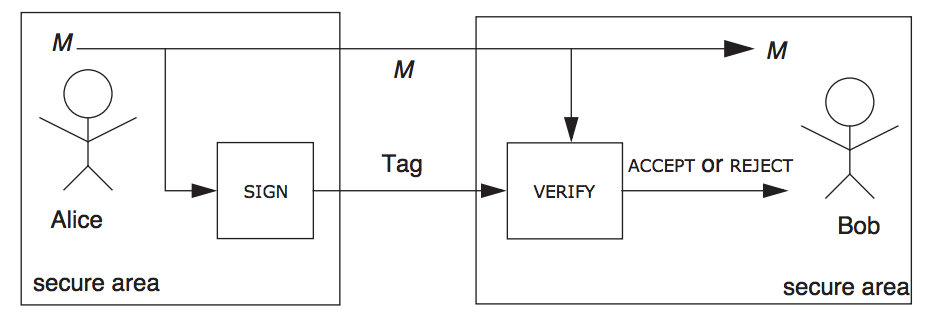
Authorization
This is the process the server uses to determine who has the right to do what. Authorization works for file access as well as what process can be run. An OS has a list of users, and their access to these files and processes can be determined by the creation of Access Control Lists. These lists group users, which groups are then assigned permission access. This is the standard way of managing authorization. These permissions are further emphasized in role-based access control, which assigns a user specific permission to a file. The general workflow for authorization checking in unix is as follows:- If the UID (User ID) of the process is 0, the process has necessary permissions.
- If the UID of the process matches the UID of the file owner, the kernel checks the permissions in the ACL entry for the user.
- If UIDs do not match, but if one of the process’s GIDs (Group ID) match the GID, the kernel checks the permissions in the ACL entry for group.
- If none of these conditions hold, the kernel checks for "other" users in the ACL entry.
Authorization is generally about who can do what, and using these permissions helps make this more relatable to how things work in the real world.