Lecture 18. Confidentiality, authorization, and protocols
Authors: Setiawan Makmur
----Authentication----
3 Ways to Authenticate
1. Based on WHO the principal is eq. Retinal Scan, Brain Scan
2. Something the principal HAS eq. Physical Key
3. Something the principal KNOWS eq. Password
Authentication protocol
External Authentication
- Stricter checking
- Slower
Tend to be stricter to protect system from foreign agents such as civilians to military facility
Eq. Passwords
List of possible attacks on passwords and ways to mitigate
- Dictionary of common passwords: Limit number of attempts
- Social Engineering: Not relying on KNOWS and HAS authentication
- Sysadmin leaking password: Prompt user to change password or encrypted passwords or "Salt" the password by adding random characters to the password, only internal system knows which characters are non-legit, eq. 12345&H7 where &H7 is the salt
- Password snoopers stealing information between client and server: Encryption between client and server or server authentication to client via certificates
Internal Authentication
- Secondary to External Authentication
- Fast checking
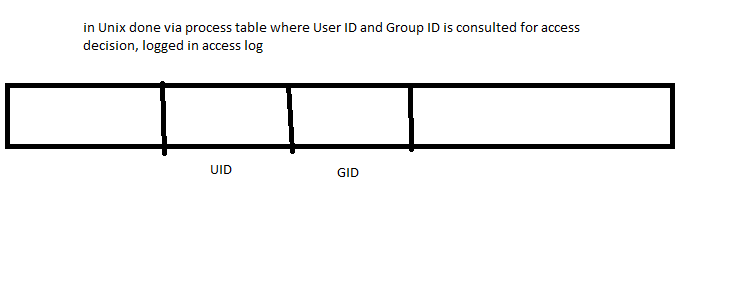
----Authorization----
Once authenticated, we would like allocate file permissions to principals, a possible implementation is the following 3d array
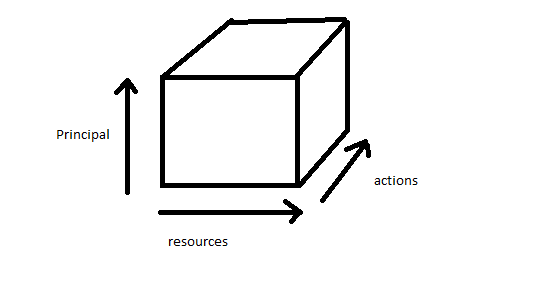
- For every principal, we would increase the size of the Z axis
- Correspondingly every file needs to be represented in the X axis
- A single permission-able action is represented in the Y axis
- THE SIZE NEEDED FOR THIS REPRESENTATION BECOMES OVERLY BIG
An alternate approach
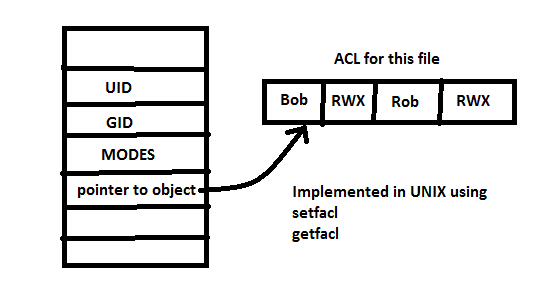
Access Control Lists (ACLs)
Files have owner + group + modes + ACL.
Modes are operations allowed for each category: self, group, and others.
ACL is implemented for more permission flexibility illustrated below.
Processes have owner + group.
Catch with ACLS with UNIX permissions
- Long-term users have access to many resources
- These individuals are granted too much power they'd rather not have, i.e permissions to files they rather not modify in current run
- Hence they would like to assume 'Roles' instead such as 'Grader', 'Course Designer', 'Software Developer'
Capabilities
We can control access to an object by encrypting a pointer to object.
This means we can send capabilities over networks for others to have access the same file without committing internal changes
They are similar to keys to your files.
Hence we don't need kernel anymore to control protection.
----Trusted Software----
Question: How can you trust the system you are running on?
Read Ken Thompson on UNIX
"Reflections on Trusting Trust