CS 111: Lecture 17 - 5/27/10
Thursday, May 27, 2010
By Emily Chen & Silas Lam
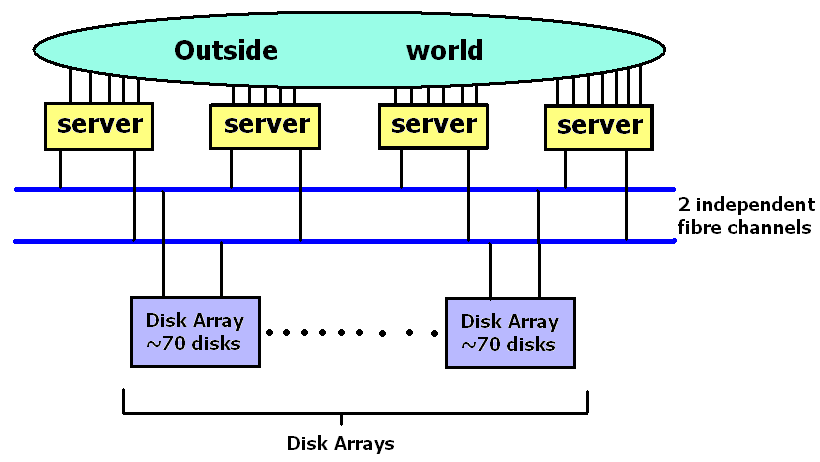
NFS Performance (spec.org)
SPECsfs2008_nfs.v3
HP BL860c i2 4-node HA-NFS cluster (April 2010)
HA -> Highly available
4 servers (each with 2 boot drives + 192 GiB RAM)
8 disk controllers (each with 2 GiB cache)
4 FC switches
16 disk arrays
1472 drivers, each with 72 GB, 15 KRPM
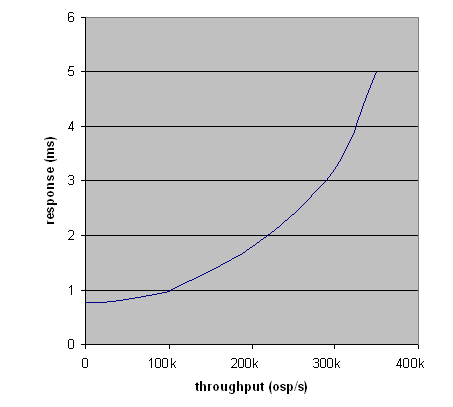
· Still faster than disk access on a local disk (assuming that most disk have response times of 20 ms)!
· Expensive though...
NFS Security
Client A:
$ sudo sh
# cp /bin/mount /nfs/eggert/mount
# chown root /nfs/eggert/mount
# chmod u+s /nfs/eggert/mount
# ls -l
-rwsr-xr-x …
Client B:
$ /nfs/eggert/mount ______
· Client A wants to share access to other computers, like Client B
· Anyone with root access on Client B can do anything on the server (as root too!)
o What if Client B was a laptop owned by someone else that you don't totally trust?
· Assumes all root-access people are clients that are trusted
o Doesn't work in general though…
o Only works in centrally-managed clusters
So we need a better approach:
· UID Re-mapping
o If client asks server for access and says that user is root, then server doesn't trust the client and uid is routed to "nobody"
· uid 0 (root) -> uid 65535 (nobody)
§ Note: 65535 is a made-up number
o Problem: Client can still pretend to be anybody else! Authentication needs to go beyond uids across the wire
o Problem: What if user "eggert" exists on Client A as uid 59 and also exists on Client B, but as uid 4625?
· Logging in from Client A won't allow you to see your own files that were created using Client B
Security
· You need to think about it right from the beginning
· Can't easily be retrofitted
· Real-world meaning: defend against attacks via force + fraud
· Virtual-world meaning: defend mostly against fraud (although we can't forget about force!)
· Main form of attacks
o Against privacy
· Gaining access (like getting your SSN)
o Against integrity
· Changing data (like changing the grades of a student)
o Against service
· Denial of Service (DOS)
· To solve this problem
o Disallow unauthorized access
· Hard to test for!
o Allow authorized access
· Much easier to test in the real world
o Both of these goals are conflicting though...
Threat Modeling + Classification
· Some things to watch out for
o Insiders
o Social engineering
o Network attacks
· Buffer overruns
§ Getting worse with time
§ E.g. conficker (estimated 7 million infected computers)
· Viruses
§ Drive-by downloads
· Denial of Service
o Device attacks
· USB / CD-ROM / etc
o Etc
Functions for Implementing Security Mechanisms
· Authentication -> passwords
· Authorization -> permissions on files
· Integrity -> logs, checksums
· Auditing -> logs
· Correctness
· Efficiency -> otherwise people won't use it
Authentication
o Prevents masquerading
· Types
o External -> outside participants
· Tends to be more expensive and suspicious
o Internal -> insiders
· Goal: Cheap and efficient
· Usually relies on external authentication already being done
External Authentication
· Need a trusted login agent
· How to authenticate?
o Based on what the principal knows
· Passwords
§ Can be guessed
§ Defense
· System-supplied passwords
· System guesses the password; if it's too easy to guess, then refuse to allow it to be a password
§ Can be told… (breaks authentication)
§ Network snoopers: steal the password while it flies past you on the network
§ Fraudulent server: Set up a website that looks exactly like another one, and people will log into your site with their real credentials
o Based on what the principal has
· Physical tokens (like a chip in your car key)
§ Can be lost
o Based on who the principal is
· Retinal scan
· Thumb prints
Internal Authentication
· OS records who you are efficiently
o In process descriptor: uid, gid, effective uid, effective gid
· What's the reason for the effective uid / gid?
§ Let's authorization work at the user level instead of the OS level
§ Let's the program do any authorization algorithm it likes
o Consulted for all access checks
· open () (and any other operations on files)
· kill ()
o System call to change uid: setuid (int )
Authentication Building Blocks
· Cryptographic hash functions
o Hash_function (key ) = value -> this is cheap
o The inverse is expensive
o Remember, many keys can map to the same value!
o E.g. SHA1 (key) = H (H is 160 bits)
· Symmetric encryption
o Shared private key K
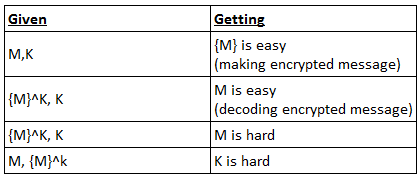
o Problem: key management is tricky
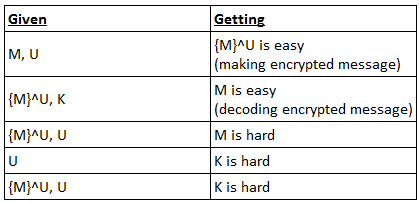
· Asymmetric encryption
o Public key systems
o Define:
K = private key (known only to sender)
U = public key (shared to recipient)
M = message
· HMAC
o Assume a shared secret key K
o Send SHA1 ( ( K^pad1) + SHA1 ( (K^pad2) + M )) + M
· + is concatenation
· ^ is XOR
· Typically use a multiphase approach
o A sends "{NonceA + I'm A}^UB" to B
o B sends "{NonceA + NonceB + I'm B}^UA: to A
o A sends "{NonceB + K}^UB to B
· K in this case is a shared secret key for this transaction
o Nonce-> some kind of special identifier for this session so that A knows that the msg from B is really from B
· ssh
o .ssh/id_rsa.pub -> public key
o .ssh/id_rsa -> private key
o .ssh/known_hosts -> log of whoever has connected along with their keys
o Is a point-to-point system
· Virtual network atop an untrusted network
· Pain to do, since you each computer that wants to connect needs to setup with all these things
· Via ssh -> problem with setup is O (N^2)
o Used more in informal networks
· IPsec
o Much bigger overhead in network infrastructure
o Sets up a virtual network on top of untrusted network and is better than ssh at doing it!
o Uses internal authentication in virtual network
o Uses external authentication to setup virtual network
o Used more often in corporate networks
Covert Channels
· You can bypass security if you really want to
· Example:
Process 1 owned by User 1
Process 2 owned by User 2
· How can U1 communication to U2 if there is no network access and no common servers?
· Use other stuff like CPU load levels or memory allocations to send bits of data to other processes
o Let's say that P1 receives a 1 if the CPU load kicks up to a certain level, and 0 is if it reaches another level. P2 can send 0s and 1s by changing the CPU load now!
o This bypasses all the permission settings and other OS stuff