Lecture 18
Professor Eggert
June 5, 2012
Author: Michael Bonilla
Authentication & Encryption
Kerckhoff's design principle for crypto-systems: minimize what needs to be kept secret.
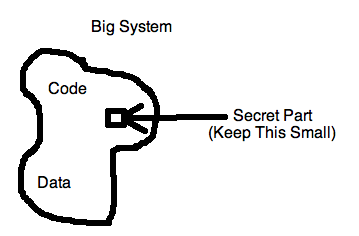
e.g. ssh: The private key is the only secret part. Public keys and known hosts are not kept secret.
ssh Transport Layer
Initial key exchange is typically RSA, authentication reoccurs every hour.
Above this is the user authentication layer:
|
Public Key:
|
Password:
|
|
Can find or guess passphrase, but attacker would still need access to system to decrypt private key
|
Can be guessed or found
|
Problems of ssh as a protocol
-
Tempting to use passwords (less secure)
-
Heavyweight operation to get connection
-
Has trouble scaling to corporate environments
Internet Protocol Security (IPsec)
-
Much larger and grander than ssh
-
Key distribution and management built-in
-
Tunneling is common and key (VPN)
Access Control (Authorization)
Goals:
-
Privacy: Don't let users read files they shouldn't have access to
-
Integrity: Don't let users write to files they shouldn't have access to
-
Trust: Whether or not a user should delegate authorization to other programs
Basic questions when designing access control model:
-
What is your security model?
-
Objects
-
Principals
-
Rights
-
What are the threats?
- Mostly worried about insiders
Big Machines
-
Many resources
-
Many users
-
Many operations
-
Need efficient way to answer the question - "Can user 'Eggert' write to file 'foo.txt'?"
3D bit array - Each bit represents if user z can do operation x to file y.
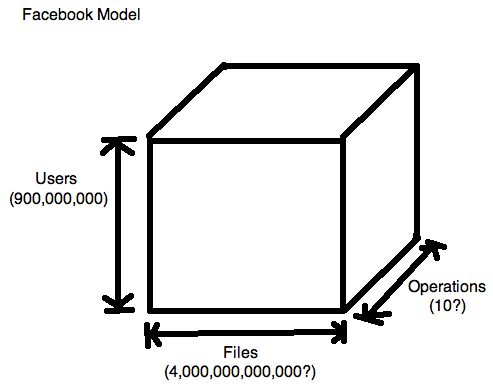
Each bit in this array must be correct at all times or there could be serious issues (access by unauthorized user or authorized user unable to access)
Common patterns for access control:
-
Simple: Unix Model
-
3 types of user for each file/directory
-
Owner
-
Group (Small defined group of users)
-
Other (Everyone else)
-
3 types of operation for each file/directory
-
r - read
-
w - write
-
x - execute for file, search for directory
-
Problem: Who can add/remove people from a group with access to a sensitive file?
-
All users? - Obvious security problems, anyone can add themselves to any group
-
Root? - Now sysadmin must be alerted whenever someone needs to be added to or removed from a group
-
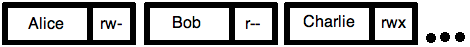
ACL (Access Control List) Model
-
Associated with each file is an ACL which control access to that file
-
Owner of object can manipulate the ACL for that object
-
ACL is part of file's metadata
-
Use syscall to change it
cd /u/class/spring12/cs111
set facl -r -m user:alice.rwx
-
Advantages:
-
More flexible
-
Easy to admin
-
Problems:
-
More overhead (due to metadata)
-
Users tend to accumulate rights but never give them up
-
Become targets for attackers
-
Programs that run as user should be more limited
-
Role-Based Access Control (RBAC)
-
Used in Active Directory, FreeBSD, Solaris and others
-
Users can assume roles
-
e.g. Eggert can be:
-
Professor
-
sysadmin
-
Student
-
Rights are associated with roles rather than directly with users
-
When user assumes a role, they gain rights and privileges of that role and give up the rights of their old role
-
Multiple sessions may have different roles for a single user
-
Capabilities
-
While ACLs reside next to data, capabilities reside next to the process that's operating
-
Handle which gives user the right to access an object
-
Access rights found in file descriptors
-
Advantages & Disadvantages:
-
+ faster: rights can be cached
-
- revoking rights is more difficult



