CS 111 Lecture 18
Confidentiality, Authorization, and Protocols
Written by
Richard Liu
rgliu@ucla.edu
Security Techniques
Imagine a world where houses had no locks and doors did not require keys to open. Nowadays, computers are every bit as important as our own homes are, holding a lot of secrets and personal information within their hard drives. Thus, computers need their own "locks" and with that comes techniques to keep items within a computer secure.
One obvious way to keep information secure is through passwords. Passwords are phrases or keys that are required as input before the user is allowed to access certain information or even log onto the computer. We of course would not want these passwords to be easily guessed, and therefore the more complex the password the better. It is actually not uncommon to see certain operating systems actually verify upon creation that a password is strong enough.
However, no matter how secure a password may seem, there are always ways to attack systems and to break passwords.
Brute Force – the most direct approach involves guessing all the possible combinations of character until the correct one is entered. The obvious flaw with this is that the difficult of guessing exponentially increases relative to the length of the password. To easily avoid this, systems can do things to slow down the guessing, such as only allowing a few attempts at a time, or pretending to take a long time to process each input
Differential Attack – This concept suggests that as the input changes, certain things about the output changes as well, such as response time, power consumption, etc. For example, a longer input may consume more battery power on a mobile device than a one character input would. To avoid these kind of attacks, you can make sure that regardless of input, that the output will always stay the same. This usually means slowing down response time of smaller inputs to match the response of larger inputs, but at the price of security, this seems negligible.
Network/ Video Snooping – another direct approach. This involves physically looking at keystrokes, or logging them through remote means such as a virus. To solve this, frequently scan your computer for malware and always make sure no one can see what you are typing when you are in public
Set Up a Fake Server – when a user goes online, replace a webpage with a similar looking webpage that asks for log in information just as the original webpage would. However, in this case, the log in information would be sent to the attacker. To avoid this, always make sure that links you follow are direct and reliable.
Authentication
There are two different kinds of authentication: external and internal. External authentication refers to logging in to an actual computer through multiple means of input such passwords, personal information, IP address and/or fingerprint scanning. Once logged in, there is internal authentication which keeps logs of user actions for future review. Internal authentication also gives the user an established ID within the system to authenticate them to additional files and resources. Think of external authentication as when you enter a federal building. At the door you are asked for identification, they check to see if your name is in the system, and if you pass, they let you in. Internal authentication is relatable to a badge they give you, which depending on clearance, will let you in through certain doors within the building.
Giving and Taking Privileges
So who determines who is allowed to access what? The first answer that comes to mind is the owner of course! But what if we want to change ownership of a file?
We have the command chown which is used on Unix-like systems and allows a super-user to change the owner of a file. Members within a group can change a file’s group ID for that specific group as well. It also used to be that you could give files away using chown, however this is not allowed anymore, due to issues involving meeting disk quotas (giving away files to increase disk capacity).
What is a super-user? In Unix OSes, it is more commonly known as root, which is a user that has rights and permissions to everything within a computer. Obviously, this is an extremely powerful position, and therefore if an attacker gained control of the root account, it would be horrendous.
The man page describes chown as simply “change file owner and group”. The format is chow [option] [owner:group] [file] where you would change the owner or group of file to owner or group.
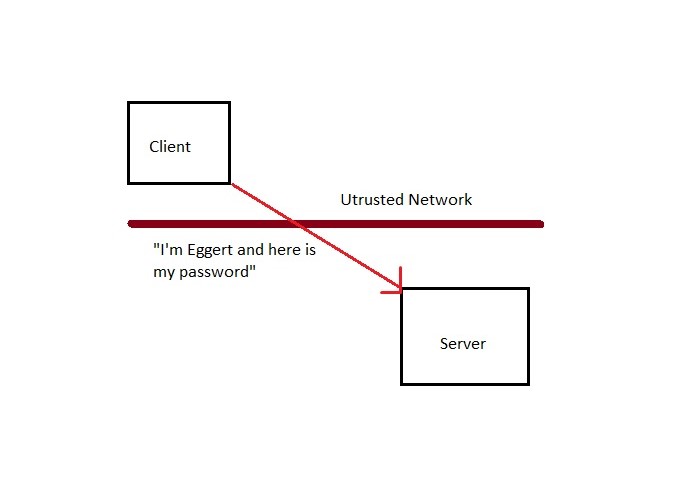
Protecting Yourself on an Untrusted Network

Let’s say you want to access a server through a network that you are not familiar with, such as one at the library or at an airport. Since we are unfamiliar with this network, the chances of an attacker lurking to snoop personal information and logins are higher. There are several ways to prevent that, one of which involves a cryptographically secure hash function.
We can think of a hash function like a mathematical equation: you receive an input x and you get a result of H(x), where H is the hash function itself. The idea of a hash function is to create a hash value out of an input which is ideally impossible to invert. However, this is unfortunately not perfect (not yet!). If a hacker has access to whatever network you are on, it would be possible for them to obtain the hash function itself and utilize the output through what we call a replay attack. This means that the hacker does not really care what the input was, as long as they can utilize the output and pass it off as their own later on.
Another method is what we call a shared encrypted key. The client and the server communicate and each of them have a key which allows them to decrypt whatever message is being sent. However, this has the same disadvantage as a hash function and is still vulnerable to a replay attack.
To avoid this we use what we call a nonce, which is a random bitstring. The user and client each agree to a nonce and include the nonce in the input of the hash function, and therefore the server will know if the user is not actually the user by checking the nonce.
Now that we have effectively authenticated the client to the server, how do we protect the actual message that the client has to send. To do this, we use the concept of hash message authentication code (HMAC). We will assume a message ‘M’ and a previously distributed private key ‘k’ and an arbitrary value to both sides which we will call ‘pad’. The way this works is shown below. ‘^’ is bitwise XOR, ‘~’ is cat and SHA1 is the secure hash function.
SHA1(( k ^ pad1 ) ~ SHA1( k ^ pad2 ) ~ M ) = MSG
This comes out with MSG which is essentially the same as a hash and allows us to come up with a secure message.
Why do we need more than one call to SHA1 however? SHA1 is a reliable hash function, but that just makes using SHA1 twice all the more secure, and less prone to a replay attack.
Authorization
Authorization comes up with who has the right to do what. We can visualize who can take what actions through a 3-dimensional space of Boolean values where 1 is when permission is granted and 0 is not.
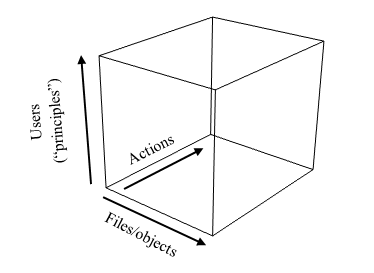
As we can see, this becomes more and more extensive as the number of users, actions and files/ objects grow. To make this structure more compact and more efficient, we approach it with access control lists.
ACLsis the idea of granting permission to a whole group of users, where the group can be created only by the root. ACL is the standard approach to authorization.
The last thing with this cube is the idea of Role-based access control (RBAC). The idea of this is that each user has a role, and through that role, they are granted certain permissions to perform actions on specific files/ objects. This compacts all permissions into a grouping and makes delegating a lot easier and there will be a less likely chance of accidentally giving someone unprecedented permission.
“The more complicated a system is, the less secure it is” – the idea that more options leaves more room for exploitation by an attacker
Good Luck on Finals!