Why Study Operating Systems?
Example OS Problem 1
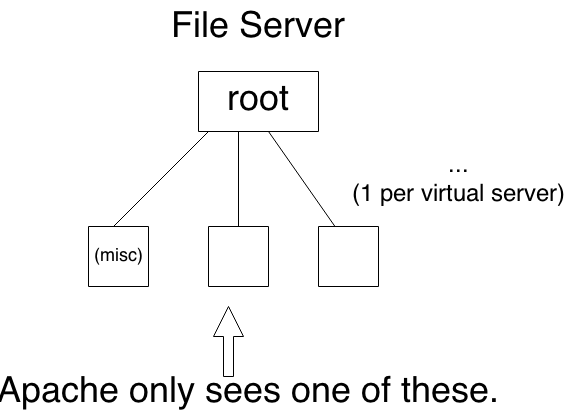
Background: N virtual servers run atop a real server with a file system. One directory exists for each virtual server in root. Users of one virtual server can only see the contents of that virtual server’s directory.
Virtual servers are backed up from the server (which has root access) using the command:
tar -cf of /dev/rmt (tape storage device). This walks through the entire tree, finds all files, and stores the files sequentially to tape.
Virtual servers (e.g., virtual server 5) can be restored by technicians using the command: tar –xf /dev/rmt/vm5. This should only grab files found in sub-tree vm27.
ln -s ../vm6/etc/passwd myfile. This doesn't work because if you try to cat /myfile, the system resolves to no such file.The exploit:
cd /- Make a regular file:
echo foo > myfile - While the virtual server is being backed up (tar is being run):
- Remove regular file:
rm myfile - Quickly replace regular file with a symbolic link to a file located on a different virtual server:
ln –s /vm6/etc/passwd
- Remove regular file:
- After the backup is done, call and ask a technician to restore your virtual server, because you 'accidentally' wiped all of your data.
Example OS Problem 2
Background: The DNS (Domain Name System) maps URL addresses to IP addresses. Root servers located around the globe resolve URL requests down a certain number of levels. Root servers know about .edu and ucla.edu, but may not know about cs.ucla.edu, so they would ask a subsidiary server (e.g., dns.ucla.edu) to resolve cs.ucla.edu.
The problem with this system was that it took too long to resolve URL requests. The browser would appear hung up during the time it took to resolve a URL request. To speed up the URL resolution process, DNS servers were given a cache to store recently resolved addresses.
- Ask a DNS server to resolve a URL address not within its cache (most likely an uncommon URL, for example llb.com)
- Send a forged IP address to the DNS server at the right time--before the root server's response is received, so that the DNS server will store the forged IP address in its cache.
Here, only one URL can be hijacked at a time. However, in 2008, Dan Kaminsky discovered how to make the attack more plausible by hijacking an entire domain instead of individual IP addresses. There is not yet a complete fix for this vulnerability.
By studying operating systems, you can avoid such flaws in your software.