CS 111 Operating Systems
Scribe Notes for Winter 2012 Lecture 4
By Vahe Musinyan & Arman Abrahamyan
HARD MODULARITY
How to implement hard modularity?
Let us consider two ways:
-
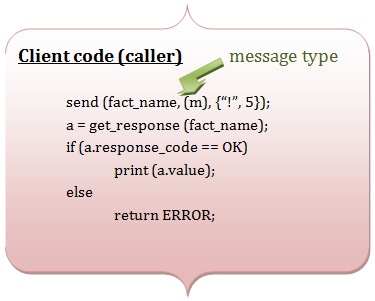
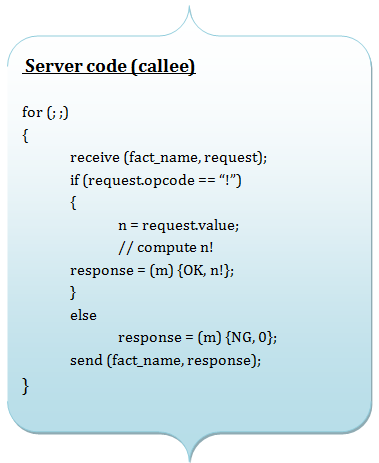
Client - Server organization (We run each module on different computers or Virtual machines)
-
Virtualization
Suppose we want to calculate a factorial function.
 |
 |
||||||||||
Pros:+ Hard modularity: client and server are protected from each other |
Cons:- Slow (latency between modules) |
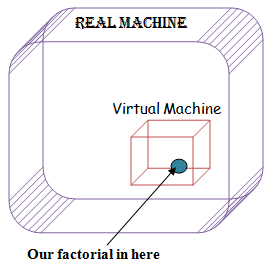
Virtualization
We want to create a "virtual machine" to run our untrusted codes there. In this case we can have one real machine that creates two
virtual machines. All disasters will happen in virtual machine and the real machine will not suffer from errors or other problems.
Write an x86 emulator
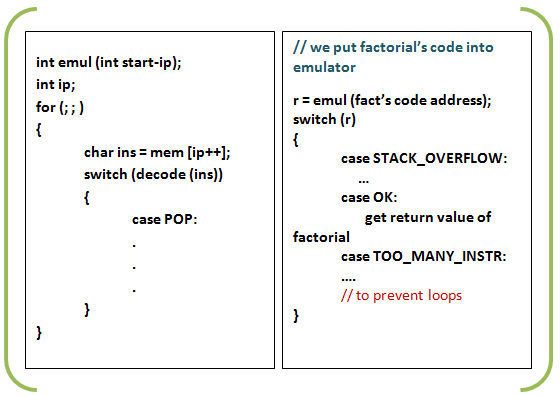
Pros:+ Gives hard modularity |
Cons:- Wayyyyy too slow |
Hardware assists to make our emulator go faster
Here Real machine's architecture is approximately equal to Virtual machine's architecture.
What we need:
- Real machine needs to take over whenever the virtual machine screws up. The virtual machine should not be able to implement and call privileged instructions.
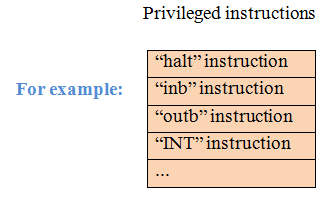
- Real machine should take over after some sort of time interval has expired. This could prevent a virtual machine from going into infinite loops.
- Some way of limiting memory access only to locations in the virtual machine.
OTERWISE - run at full speed (emulator will run at a speed of Real machine).
This whole process is called "virtualizable process".
From Application's point of view
- Normal computation: a = b*b - c*c; // we want to implement this at full speed
- System call :
write (1, "hello, world\n", 13); // no 'inb' or 'outb' here
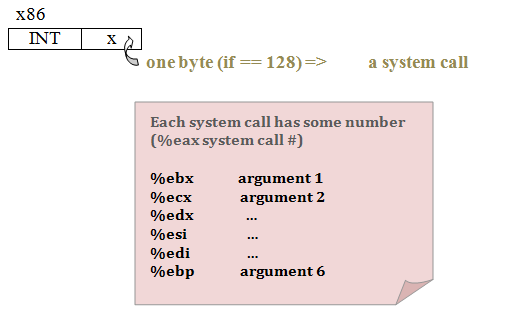
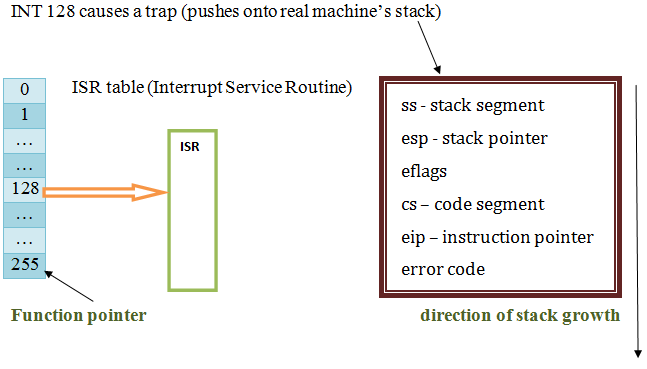
*implement this via - a deliberate crash (INT instruction) // INT means interrupt
If you have more than 6 arguments for function, that means something is "wrong". Try to minimize it up to 6.
Write function implementation (runs on Virtual Machine)
ssize_t
write (int fol, char *buf, size_t bufsize);
{ ….
Asm ("int 128");
… }
Virtualization is only one-way protection
![]() But faster than client/server on a typical hardware
But faster than client/server on a typical hardware
OS organization
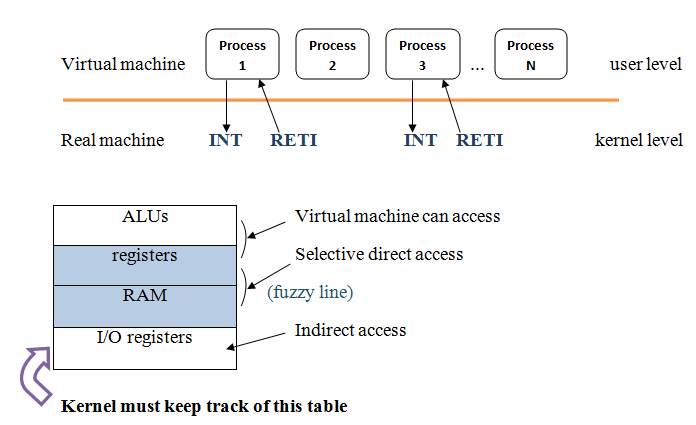
RETI is the function that returns from system interrupt handler into the process that has caused the interrupt.
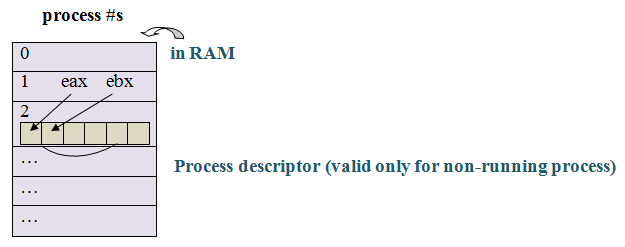
Why would a process not run? (on a single core machine at most 1 process can run).
In some cases we do not need to copy all registers, for example n = getpid().
Protecting memory is hard, for now we will skip this. This will be done later in the course.
Ways for applications to create/destroy processes
To destroy:
1) a process can issue a privileged instruction "halt"
2) exit (23); // the number in exit () shows the status (8 bit code)
To create:
1) p = fork (); // clones the current process
except:
p = child's pid in parent
p = 0 in child
p = -1, if ERROR