Computer Science 111: Operating System Principles - Lecture 1
Prepared by Eric Mallare and Hong Shin for a lecture by Paul Eggert on January 7, 2013.
Table of Contents
Class Logistics
Course Website
Textbook
Principles of Computer System Design, by Saltzer and Kaashoek.
Requirements and Hours
| Prerequisites | Recommended | Official Hours | Actual Hours |
|---|---|---|---|
|
|
|
|
Grade Breakdown
| Weight | Assignment |
|---|---|
| 1⁄9 |
Midterm
|
| 2⁄9 |
Final
|
| 1⁄3 |
Labs
|
| 2⁄15 |
Minilabs
|
| 1⁄12 |
Design Problem
|
| 1⁄15 |
Current Event Paper
|
| 1⁄20 |
Scribenotes
|
Late Policy
Points taken off = 2N-1, where N is the number of days late. This policy applies even if a fractional part of a day was used. Of course, for N ≤ 0, zero points will be taken off.
Drop-dead date
All assignments must be submitted by 23:59:59 on Friday, March 15, 2013. No work will be accepted after this date.
Systems and Operating Systems
A Quote From The Economist
"We don't offer a ready-made program, but an entire operating system."
M. Weisband, Pirate Party (Germany)
This is an example of how the term 'operating system' is used today. Perhaps the word is in the process of vernacularization?
What is a System?
Oxford English Dictionary (Original--1928)
- An organized or connected group of objects.
- A set of principles, etc...; a scheme, method.
Greek Etymology
- σύστημα (sýstima) - Organized whole, government, constitution, flock of birds, musical interval, group of connected verses in a poem.
What is an Operating System?
Encarta (2007)
- Master control program in a computer.
Wikipedia: ver 531774181 (2013-01-07)
- A collection of software that manages computer hardware resources and provides common sevices for computer programs.
Principles of Computer System Design (2009)
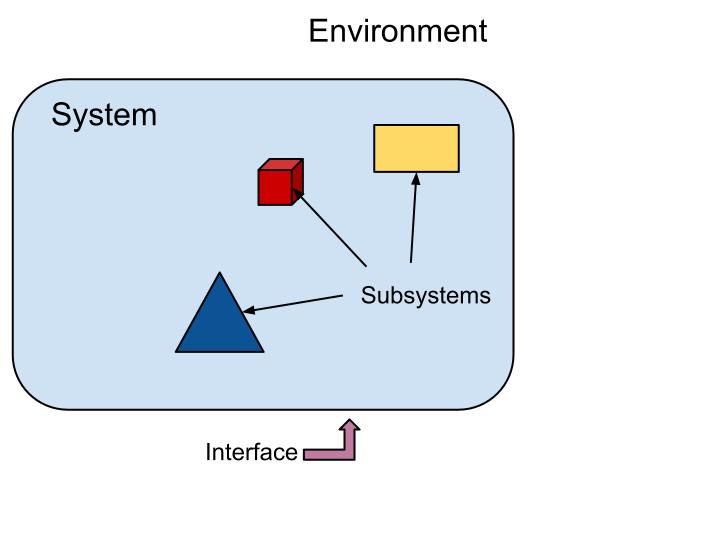
- A system is a set of interconnected components that has a specified behavior observed at the interface with its environment.
Notice that the focus now is the interaction betwixt the environment (e.g. users) and the system via the interface.
Problems with Computer Systems
Tradeoffs
Waterbed Effect: Improving one property will negatively affect the others.
Example: Merge Sort
- Want to sort 1 GiB worth of 512 byte records using Merge Sort.
- There is overhead of copying data into memory during the sort
- If the pointers to the records are sorted instead, we can speed up runtime.
| Pros |
|
|---|---|
| Cons |
|
Therefore, from this example, we see that aggressively speeding up the runtime costs us in other areas--we have the cost of dereferencing pointers and the overhead of additional memory that is required to hold the pointers.
Example: RSA Secure ID
- Use a combination of password and RSA ID.
- Attackers will need both for access
| Pros |
|
|---|---|
| Cons |
|
Thus, in this example, we see that although having an RSA Secure ID gives us an extra layer of security, we need to use it every time we want to access our account. This may become tedious if we need to log in frequently. An optimization in one place almost always degrades another aspect elsewhere.
Incommensurate Scaling
Not all properties improve and scale at the same rate.
Economies of Scale - Pin Factory
An example of economies of scale is Adam Smith's example of the pin factory. Say that there is a village. In this village, the townsfolk need pins for everyday life. One way to approach this problem is to have the villagers manually make the pins themselves every time the need arises. However, Smith proposed an better solution. He stated that a factory that specializes in making pins would be able to pump out more pins at a cheaper cost per pin. Since the cost per pin scales well with the number of customers, this is an example of economies of scale.
Diseconomies of Scale - Ethernet Switches
- 4-port and 8-port Ethernet switches are fairly cheap.
- Creating a 512-port Ethernet Switch is very expensive.
We notice that for a small number of ports, Ethernet switches are cheap and easy to obtain. However, we notice an opposite trend compared with Adam Smith's Pin Factory: as the number of ports increases, the price of such a switch increases dramatically. Since the price does not scale well with the number of ports, this is an example of diseconomies of scale.
Emergent Properties
Unanticipated properties due to scaling.
Napster and Torrents
UCLA got a massive boost to network speed. Professors and faculty were pleased that the students would have much speedier access to the Internet. For example, scholarly articles would be no problem to download. However, students misused this privilege and hopped onto torrents and Napster in order to illegally obtain songs, games, movies, and shows.
Computer Worms
When the internet was first made, everyone knew each other for the most part. Therefore, using the Internet for malicious intent was out of the question. However, with the exponential expansion of the internet, worms were developed and infected many unwitting machines. Of course, the machines were ill-prepared for such an event, since it was completely new and unanticipated.
Tacoma Narrows Bridge
Engineers had built many moderately sized bridges that could withstand earthquakes and other natural phenomena. The Tacoma Narrows Bridge was special because nothing of its scale was ever constructed. Thus, the builders never predicted that the wind would match the resonant frequency of the bridge. This lack of foresight cost them the bridge on November 7, 1940.
Propagation of Effects
Seemingly small and/or unrelated occurrences in one area may have large ramifications in another area via a chain of events (e.g. butterfly effect).
Ronald Reagan's Presidency
In the 1930's, a Hollywood actor got depresed and shot himself. A radio man was hired in his stead--Ronald Reagan. Some say that Reagan would not have become president if he did not gain early exposure via this movie.
These sort of things happen naturally all the time in chaotic systems.
However, note that these can also happen in engineered systems:
Japanese Encoding
Although a byte was enough to encode English, it isn't enough for Chinese, Japanese, and a slew of other languages with myriads of symbols. Therefore, Microsoft decided to use two bytes to represent Japanese characters. If the first bit is switched on, the rest of the bits will encode the actual character. However, there was a completely separate module in Windows that parsed filenames (e.g. C:\ProgramFiles\).
Unfortunately, this parser never took the multibyte encoding into account. Therefore, if we tried to copy a file to a directory, and the directory was written in a language that requires a multibyte encoding, we could get a strange error: "no directory named \usr\bin\[?]" If the bits in the second byte arranged themselves in such a way to form a '\', the filesystem would get confused and think that you are trying to copy a file to a directory that doesn't exist.
One way to fix this is to change the filename parser to recognize that its in English mode or Japanese mode.
A better way to fix this is to not use an encoding where random bytes look like ASCII characters. For example, we could use UTF-8. The downside to this is that it is less efficient because we use more bytes to encode characters.